In today’s digital landscape, securing your AWS (Amazon Web Services) cloud infrastructure is paramount. With cyber threats becoming increasingly sophisticated, ensuring the safety and integrity of your data on the cloud is non-negotiable. To help you fortify your AWS environment, we’ve compiled a list of five indispensable steps that every organization should take to bolster their cloud security defenses.
1. Enable Multi-Factor Authentication (MFA) 🛡️
Activate Multi-Factor Authentication across all AWS user accounts to add an extra layer of security beyond passwords. MFA requires users to provide an additional form of verification, such as a unique code sent to their mobile device, making it significantly harder for unauthorized users to gain access to your AWS resources.
Here are step-by-step screenshots :
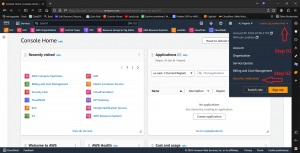
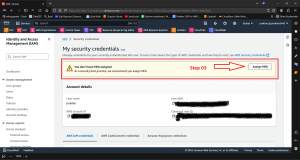
2. Implement Least Privilege Access 🔒
Adopt the principle of least privilege to restrict user access rights to only what is necessary for their roles and responsibilities. By granting the minimum level of permissions required, you can minimize the risk of unauthorized actions and potential data breaches within your AWS environment.
3. Regularly Update and Patch Your Systems 🔄
Stay vigilant against security vulnerabilities by promptly applying updates and patches to your AWS services, operating systems, and applications. Regular updates help address known security flaws and mitigate the risk of exploitation by cyber attackers, ensuring your cloud infrastructure remains resilient against emerging threats.
4. Encrypt Data in Transit and at Rest 🔐
Utilize encryption to safeguard sensitive data both in transit and at rest within your AWS environment. Enable SSL/TLS encryption for network communications and leverage AWS Key Management Service (KMS) to manage encryption keys securely. Encrypting data adds an extra layer of protection, making it unreadable to unauthorized parties even if intercepted.
5. Monitor and Audit AWS Resources Continuously 🕵️♂️
Implement robust monitoring and auditing mechanisms to track user activities, detect anomalous behavior, and identify potential security incidents in real-time. Utilize AWS CloudTrail for comprehensive logging of API activity and AWS Config for assessing compliance with security policies. Proactive monitoring allows you to respond promptly to security threats and ensure the integrity of your AWS cloud environment.
By adhering to these five essential practices, you can strengthen the security posture of your AWS cloud infrastructure and mitigate the risk of security breaches and data compromises. Protecting your assets on the cloud requires a proactive and holistic approach to security, and these steps serve as foundational pillars for building a resilient AWS environment.


